Why MFA Is Non-Negotiable in Today’s Threat Landscape
In today’s digital world, usernames and passwords alone are no longer enough to protect your organization. Cybercriminals are relentlessly targeting small and mid-sized businesses with phishing attacks, credential stuffing, and brute force logins, methods that, unfortunately, succeed far too often when only a password stands in the way. That’s where Multi-Factor Authentication (MFA) becomes essential.
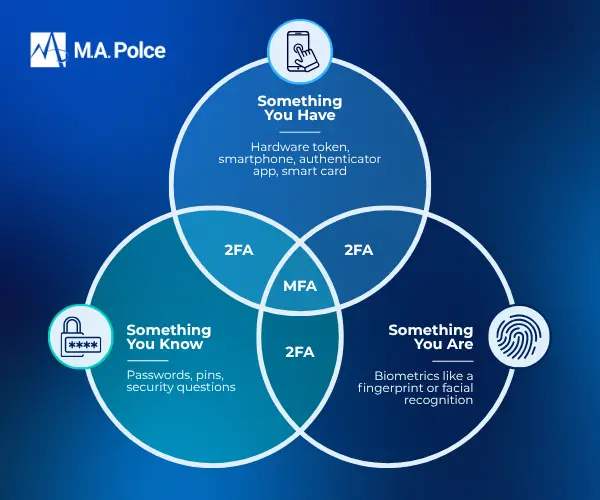
MFA adds a critical layer of defense by requiring users to verify their identity using at least two different factors: something they know (like a password), something they have (like a smartphone), or something they are (like a fingerprint). It’s a simple concept with a powerful impact. By requiring a second form of authentication, MFA can stop the vast majority of unauthorized access attempts, even when login credentials have been compromised.
For organizations of all sizes, and especially for smaller businesses that often lack large internal IT teams, MFA is no longer a “nice to have.” It’s a minimum requirement for strong cybersecurity, a staple in most cyber insurance policies, and a foundational control in nearly every modern compliance framework.
But there’s a catch: MFA needs to be implemented strategically to deliver its full value. Turning it on blindly across your environment can lead to friction for users, gaps in protection, or even compliance issues if done improperly. That’s why, in this blog, we’re sharing MFA deployment best practices that balance security, user productivity, and compliance, from understanding your environment to choosing the right MFA methods.
Know Your Environment: Mapping Access and Sensitivity
Before you can roll out MFA effectively, it’s important to assess your IT environment. Just turning MFA on isn’t enough. You must align it with how your organization actually works to protect the right systems, users, and data effectively.
Start by identifying all the systems, applications, and services your employees access regularly. This includes:
- Cloud platforms like Microsoft 365, Google Workspace, or Salesforce
- Line-of-business applications such as accounting, HR, or project management tools
- Remote access tools like VPNs or Remote Desktop
- On-premise servers and file shares
- Email systems, both cloud-hosted and on-prem
- Devices themselves, especially laptops or workstations containing sensitive data
Next, classify these systems based on the type of data they store and their role in your operations. For example:
- Does this system store customer or employee personal information?
- Is it used to access financial records, medical data, or proprietary business intelligence?
- Could a compromise here lead to significant downtime or legal liability?
This risk-based inventory allows you to prioritize where MFA should be implemented first, starting with high-impact targets like cloud email, remote access, and administrator-level accounts. It also helps ensure you’re aligning with regulatory or cyber insurance requirements, which often mandate MFA for specific types of access or data.
In our work with clients across various industries, we’ve found that organizations that take the time to map out their environment upfront are more successful in deploying MFA in a way that’s secure, sustainable, and well-received by users.
In short, you can’t protect what you don’t understand. Building this foundational visibility sets the stage for every MFA decision that follows.
Prioritize High-Value Targets First
Once you understand your environment, the next step is to prioritize where MFA will make the greatest impact, the fastest. Not all systems carry the same level of risk, and not every user needs the same level of protection. A smart MFA deployment starts by focusing on what matters most: high-value targets. Here’s where to start:
Remote Access Points
Any system that can be accessed from outside your network should be at the top of your list. This includes:
- VPN connections
- Remote Desktop Protocol (RDP)
- Virtual Desktop Infrastructure (VDI)
- Cloud-hosted applications
Remote access dramatically increases the attack surface. Without MFA, a stolen password is all it takes to walk right through the front door.
Cloud Email Platforms
Cloud-based email systems like Microsoft 365 and Google Workspace are magnets for attackers. They often serve as a gateway to calendars, contacts, documents, and other integrated services. Once compromised, an attacker can silently monitor communications, reset passwords, and launch internal phishing attacks.
It’s also worth noting that frameworks like NIST recommend prompting MFA at least every 30 days for cloud applications, even if you’ve already “trusted” the device. That extra checkpoint significantly reduces risk if a device is lost, stolen, or falls into the wrong hands.
Critical SaaS Applications
Finance, HR, legal, and customer data platforms are prime targets for both hackers and insider threats. If your business uses cloud-based tools for payroll, accounting, CRM, or supply chain management, enabling MFA for those apps is essential.
Administrative and Privileged Accounts
Your IT staff, system administrators, and anyone with elevated permissions pose a higher risk, not because they’re untrustworthy, but because the accounts they use are more powerful. Admin-level access often allows users to disable security controls, view sensitive data, or make changes across the environment. These accounts must always be protected by strong MFA, ideally using more secure methods like app-based or hardware token authentication.
Prioritizing in this way ensures your most sensitive access points are protected first, while giving your team time to scale deployment thoughtfully across the rest of your organization. It also minimizes disruption, allowing users to adjust to MFA in stages rather than all at once.
Understand Your Compliance and Insurance Requirements
As MFA becomes more widely recognized as a baseline cybersecurity control, it’s also increasingly required, not just by security best practices but by the external forces your business relies on to operate.
Cyber Insurance Policies
Cyber insurers have tightened their underwriting standards in recent years. MFA is often one of the first requirements listed in both policy applications and renewal questionnaires. Insurers want to see MFA in place for:
- Remote access to the network
- Email platforms
- Privileged accounts
- Key third-party vendors
Failing to implement MFA or only partially implementing it can jeopardize your coverage or reduce the payout in the event of a claim. Even more importantly, some policies may be voided entirely if it’s discovered that MFA was claimed but not enforced across the necessary systems.
Regulatory Frameworks and Industry Standards
Depending on your industry, there are likely specific compliance mandates that require MFA:
- HIPAA: While not explicitly stating MFA, HIPAA requires safeguards that MFA helps satisfy
- NYDFS 23 NYCRR 500: Requires MFA for any access to non-public information
- PCI DSS: Requires MFA for access to cardholder data environments
- NIST SP 800-63 & 800-171: Mandates MFA in many scenarios, especially for government contractors
- CJIS Security Policy: Requires MFA for all remote access to criminal justice data
- CMMC (for DoD contractors): Enforces MFA as part of access control
Small to mid-sized businesses are not exempt from these rules, especially those working with healthcare, financial services, government contracts, or education. Whether you’re audited annually or expected to self-attest, MFA compliance is now table stakes.
Documented Enforcement Matters
It’s not enough to say, “we have MFA.” Insurers and auditors want to see that it’s actively enforced, tested, and documented. If your policy only applies to some users or is opt-in for others, that may not meet the threshold for compliance.
As an IT and cybersecurity service provider, we help organizations not just implement MFA but also configure it in a way that aligns with both business needs and regulatory expectations. That includes helping you maintain clear documentation of your policies, configurations, and enforcement status, which is critical for insurance claims, audits, and peace of mind.
Choose the Right MFA Methods for Your Organization
There’s no one-size-fits-all approach to MFA. Today’s authentication landscape offers multiple options, and each has different implications for security, usability, and cost. The key is to match the method to your organization’s needs, risk profile, and user workflows. Here’s a breakdown of common MFA methods and where they typically fit best:
Push Notifications via Authentication Apps
Apps like Microsoft Authenticator, Duo, or Google Authenticator send a push notification to a registered mobile device. Users simply approve or deny the login attempt.
- Best for: Most users across cloud apps and VPNs
- Pros: User-friendly, widely supported, low-friction
- Cons: Dependent on mobile device availability
Time-Based One-Time Passcodes (TOTP)
These are rotating numeric codes generated by an app or sent via text/email.
- Best for: Users who may not have consistent mobile internet access
- Pros: Easy to implement
- Cons: More prone to phishing than push notifications; SMS codes in particular are less secure
Biometric Authentication
This includes fingerprint, facial recognition, or retina scans—typically used on smartphones or newer laptops.
- Best for: High-security environments and privileged users
- Pros: Convenient, fast, strong identity assurance
- Cons: Requires compatible hardware; may not be feasible for all users
Hardware Tokens (e.g., YubiKeys)
These physical devices generate one-time codes or plug directly into a device to validate access.
- Best for: Admins, executives, or users with access to highly sensitive systems
- Pros: Extremely secure; phishing-resistant
- Cons: Higher cost; logistical challenges with deployment and replacement
Single Sign-On (SSO) with MFA Enforcement
SSO allows users to access multiple applications with one login, while still requiring MFA at the initial sign-in point.
- Best for: Organizations with a wide range of cloud and SaaS apps
- Pros: Simplifies user experience; improves control
- Cons: Initial setup can be complex and may require identity provider integration
It’s also important to layer your methods based on risk and role. For instance, regular users may be fine with push notifications, while administrators might require both hardware tokens and device-based biometrics.
Ultimately, the “right” MFA method is the one that strikes the best balance of security, usability, and operational fit. As your IT and cybersecurity partner, our role is to help you make that match as seamless as possible.
Balancing User Productivity and Security
Let’s be honest, security tools that frustrate your users are tools that eventually get bypassed or resisted. That’s why it’s critical to view MFA not just as a technical control, but as a user experience design challenge.
The goal? Maximum protection with minimum friction. Here’s how to get there:
Start with High-Impact Users and Applications
Rolling out MFA in stages reduces pushback. Begin with administrators, remote users, and anyone accessing sensitive or cloud-hosted systems. Once that’s in place, expand to other users and internal applications over time.
Use Conditional Access Where Possible
Modern MFA tools can be configured to prompt users only when risk is elevated, such as when logging in from a new location, an unknown device, or during off-hours. This reduces daily friction without sacrificing protection.
Communicate Clearly and Early
Before deployment, take the time to explain the why behind MFA. Let your team know that this is about protecting them as well as the organization. Provide training, guides, and a clear path for support.
When users understand how MFA protects them from phishing and account hijacking, and that the process takes just seconds, they’re far more likely to cooperate.
Offer Device Flexibility
Whenever possible, allow users to choose between multiple MFA methods (e.g., push vs. passcode). A little flexibility can go a long way toward easing adoption and reducing IT support calls.
Don’t Ignore On-Prem Devices
In some cases, even local workstation logins should be protected with MFA, especially for shared systems or devices that store sensitive data. While more challenging to implement, MFA can be a smart investment in higher-risk settings.
By designing your MFA rollout with empathy and strategy, you build user trust while strengthening your security posture. This balanced approach helps MFA stick, and that’s the key to long-term resilience.
Extend MFA to All Access Channels
Once you’ve implemented MFA for your most critical systems, it’s time to think holistically. Threat actors don’t limit themselves to cloud apps or admin portals; they look for any weak link in your access chain. To close the loop, MFA must extend beyond obvious entry points. That includes:
On-Premises Systems and Devices
Workstations, legacy applications, file servers, and even internal dashboards can contain sensitive data or serve as stepping stones in a broader attack. While MFA for local logins isn’t always required, it is highly recommended, especially for:
- Shared workstations
- Devices used by privileged users
- Systems that store or process regulated data
Several endpoint management tools now offer integrated MFA solutions for Windows, macOS, and Linux logins.
Cloud and SaaS Applications
Many businesses deploy MFA for email but overlook other cloud-based platforms, like:
- Project management tools (e.g., Asana, Monday)
- Customer support platforms (e.g., Zendesk)
- Marketing and CRM systems (e.g., HubSpot, Salesforce)
- Financial/accounting software (e.g., QuickBooks Online)
While not all apps natively support MFA, many can be secured through Single Sign-On (SSO) or third-party identity providers. There’s often a short grace period to enable MFA after adoption—don’t wait too long and leave the door open.
Vendor and Third-Party Access
If contractors, vendors, or outsourced teams access your systems, even temporarily, they must use MFA. Supply chain attacks are on the rise, and attackers often exploit weak security practices among third parties. Enforce MFA on all remote connections and access portals. This includes:
- File-sharing platforms
- Remote support tools
- API integrations
- Admin panels provided by external vendors
BYOD and Mobile Access
When users check email or access work apps from personal devices, those devices become part of your security perimeter. Use mobile device management (MDM) and conditional access policies to require MFA for:
- New device enrollments
- First-time app access
- Device re-authentication every 30 days (per NIST guidance)
The goal here isn’t just to be thorough; it’s to ensure that MFA actually reduces your organizational risk. That only happens when every access point is covered.
Deployment Best Practices
A successful MFA rollout doesn’t happen by accident. It requires clear planning, communication, and testing, especially for small to mid-sized organizations without a large IT team. Here are our top tips for rolling MFA out the right way:
Create a Phased Rollout Plan
Avoid overwhelming your team by starting with a core group of users, such as IT staff, executives, and remote workers. Then, move through departments or roles in phases. Each phase gives you a chance to:
- Test configurations
- Capture feedback
- Adjust policies
Use Group Policies and Directory Integrations
If your environment includes Active Directory, Azure AD, or a cloud identity provider, use those tools to assign MFA requirements by group or user role. This simplifies management and ensures consistent enforcement.
Communicate Early and Often
Change management is key. Let users know:
- Why MFA is being implemented
- What to expect during setup
- How to choose a method and enroll
- Where to go for help
Empathy and education go a long way, especially for nontechnical teams.
Offer Guided Enrollment
The more support you offer upfront, the fewer headaches you’ll have later. Provide:
- Step-by-step enrollment guides
- Video walk-throughs
- FAQ documents
- Live training or office hours
Some organizations even conduct “MFA Day,” during which teams enroll together with support nearby.
Prepare for Exceptions
You’ll run into unique cases, such as users without smartphones, legacy apps that don’t support MFA, or devices in low-connectivity environments. Work with your IT provider to identify and document exceptions early and determine acceptable alternative controls (such as IP restrictions or offline tokens).
By planning proactively, your rollout will not only meet security goals but also be an operational win.
Monitoring, Maintenance, and Policy Review
MFA isn’t a “set it and forget it” control. Like any core part of your cybersecurity program, it needs ongoing attention to remain effective.
Monitor for Bypass Attempts and Login Anomalies
Most MFA systems include logging and alerting capabilities. Make sure you’re reviewing logs for:
- Failed authentication attempts
- Login attempts from unknown locations or devices
- Unusual login times or IP addresses
These can indicate attempts to compromise accounts, even if MFA blocked them.
If you work with a managed cybersecurity provider, this type of monitoring is often built into a broader detection and response service.
Review and Refresh Access Policies
Revisit your MFA policies at least annually, or sooner if:
- You onboard new applications
- Team roles or vendors change
- Compliance requirements evolve
- A security incident occurs
This review should answer questions like:
- Are all high-risk systems still covered?
- Are users still using the recommended authentication methods?
- Are there gaps in conditional access policies?
- Maintain Documentation for Compliance and Insurance
Keep records of your MFA policies, enforcement scope, and logs. This documentation can be invaluable during audits, breach investigations, or cyber insurance claims.
Provide Ongoing Training and Updates
User awareness shouldn’t stop after rollout. Regularly update your team on:
- New authentication options (e.g., passwordless login)
- Policy changes
- Security reminders and best practices
- And finally, test recovery procedures periodically. Make sure you know how to respond if a user loses access, a device is compromised, or MFA services are disrupted.
Effectively Deploy MFA for a Smarter, Stronger Security Posture
Multi-factor authentication isn’t just another checkbox; it’s one of the most effective, accessible, and widely supported security controls available today. When implemented thoughtfully, it protects your organization against the most common and costly threats, from credential theft to unauthorized remote access.
However, to truly serve its purpose, MFA must be more than a quick deployment. It needs to be:
- Aligned with your organization’s risk profile
- Integrated across all key access points—cloud and on-prem
- Supported by your users, your leadership, and your IT strategy
- Maintained through ongoing policy review, monitoring, and training
Whether you’re navigating compliance, reducing cyber insurance premiums, or simply trying to sleep better at night, MFA plays a foundational role in building long-term resilience. It’s not the only layer of defense you need, but without it, every other layer is significantly weaker.
Ready to Strengthen Your MFA Strategy? Let’s Talk.
At M.A. Polce, we help small and mid-sized organizations across all industries plan, deploy, and manage MFA the right way, tailored to their unique environment, users, and goals.
If you’re unsure where to start or want to make sure your existing MFA setup is doing its job, we’re here to help. From strategic planning to hands-on deployment to long-term support, we can guide you every step of the way. Contact us today to schedule a no-pressure conversation with one of our experts.