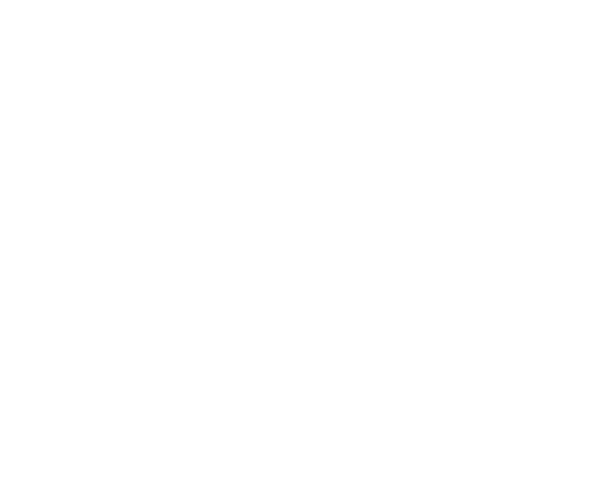Leverage the Power of Human-Led Cybersecurity Services
From foundational security to comprehensive cyber protection, M.A. Polce’s cybersecurity services strategically defend your network investments, satisfy compliance regulations, and help you develop a robust cybersecurity program.
Managed Cyber+
Assess. Strengthen. Defend.The Complete Security Ecosystem.
M.A. Polce’s Managed Cyber+ service offers organizations a supportive security ecosystem focused on awareness, growth, and alignment with industry standards. A certified security professional creates a tailored program to enhance your security posture using a blend of education, human intelligence, and advanced technologies.
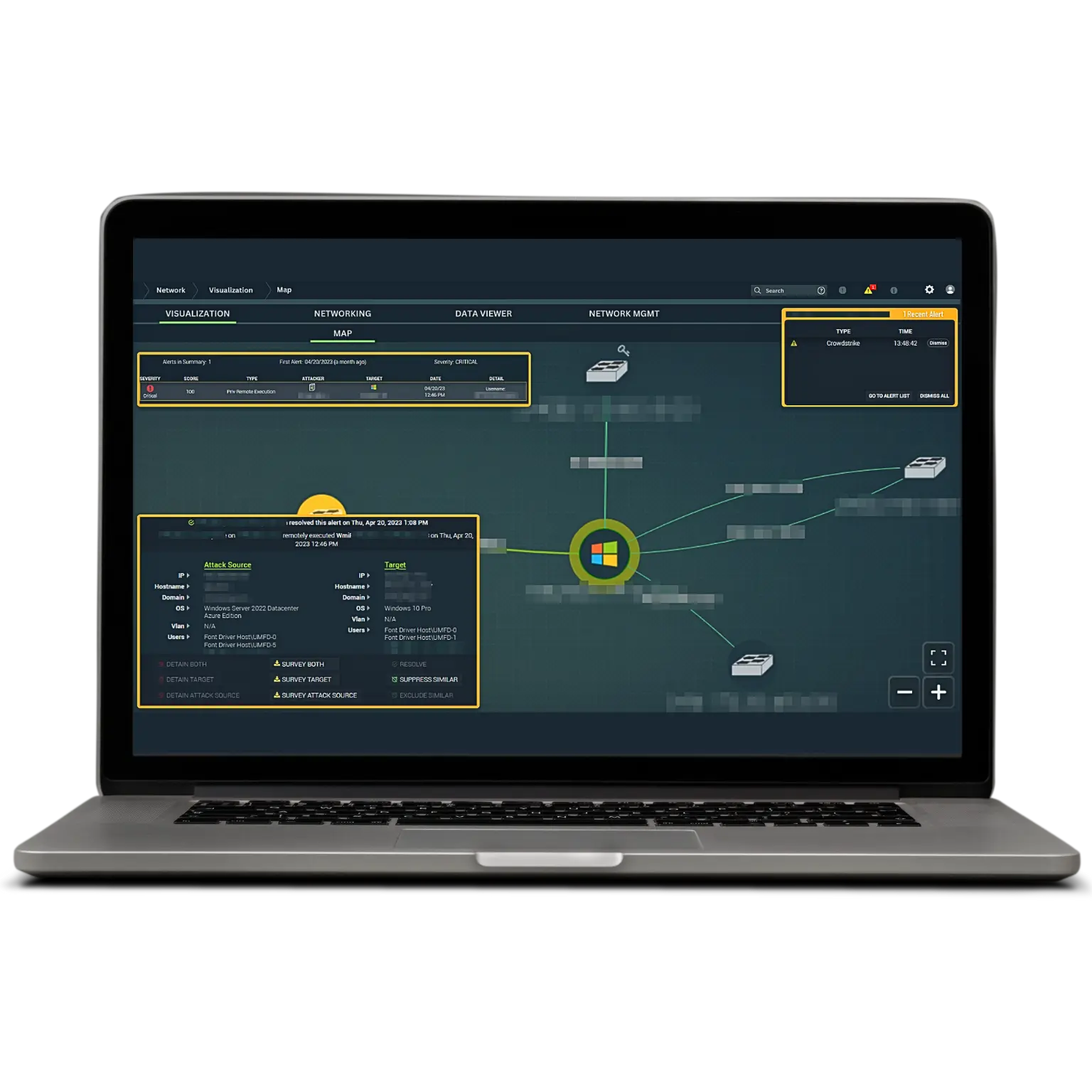
Managed Detection & Response
Defend Against Cyberattacks 24x7x365
Faster than any other solution on the market, our MDR technology harnesses metadata around suspicious events, hacker tradecraft, and remote privileged activity to catch what others miss and take real action before cyber threats can spread.

Governance Risk & Compliance
Streamline GRC Efforts
This program provides insights into your cyber risk profile, enabling you to continuously improve your security posture and ensure compliance with data security standards.
Network & Endpoint Security Services
Protect Your Network Against Cyber Threats
Network security involves protecting a company’s network infrastructure, while endpoint security focuses on securing individual devices such as laptops, desktops, and mobile devices. Both are essential in safeguarding a company’s sensitive information and preventing unauthorized access.
Endpoint Detection & Response
EmailSecurity
Syslog & Device Event Logging
Cyber Risk and Security Assessments
Understand and Address Your Cyber Risk
Cyber risk and security assessment services help organizations understand their cyber risk, reveal weaknesses in their security program, and guide resource allocation.
Security Assessment
Identify vulnerabilities that could allow threats to infiltrate. Our security analysts provide a comprehensive report for you to take corrective action and firm up your defenses. Unquestionably, a Security Assessment is one of the best first steps an organization can take.
What is a Security Assessment?
A Security Assessment analyzes critical systems based on industry benchmarks and best practices, along with a comprehensive report outlining associated vulnerabilities and the risks they pose to your organization. In addition, recommended action items are identified and clearly explained.
Today’s rapidly evolving threat landscape demands smarter and more comprehensive security measures. Security Assessments identify vulnerabilities in your IT systems and provide recommendations for improvements so you can lower the risk of data breaches.
Why do I Need a Security Assessment?
Cyber threats have become so damaging and attacks so widespread that many organizations find themselves lacking the appropriate resources to combat these threats. It’s essential to evaluate the existing security within your environment to identify risks and the effect they could have on day-to-day business operations. Our experts perform assessments that identify vulnerabilities and the steps you should take to safeguard your perimeter network, critical internal assets, remote users, and customers.
Risk Assessment
Identify, prioritize, and measure your organization’s cybersecurity risk to proactively mitigate threats. M.A. Polce’s Risk Assessment provides insight to ensure your organization is taking the right steps to protect assets, satisfy compliance, and effectively manage risk.
What is a Risk Assessment?
Risk Assessments are the building block upon which all compliance activities are implemented and measured. Performing a risk assessment ensures that security is kept at the forefront of your organization. The risk assessment starts with a questionnaire administered by one of our cybersecurity experts, and then we evaluate everything to provide risk ratings and recommendations for improvement.
Why do I Need a Risk Assessment?
Organizations may perform risk assessments because they are required to, but their true value lies in knowing how the organization is vulnerable and the path to achieving compliance and a more secure environment. The risk assessment results provide the necessary insights to build a comprehensive security roadmap that drives decisions and funding.
Penetration Testing
Determine if Hackers can Get Past Your Defenses
Penetration testing is an essential practice for businesses that want to ensure their systems and networks are secure.
What is a Penetration Test?
Pen tests are a form of ethical hacking used to test the effectiveness of an organization’s cyber defenses. The test involves an authorized and simulated cyber attack against your IT infrastructure designed to check for exploitable vulnerabilities.
Why do I Need a Penetration Test?
Penetration tests are needed to provide evidence that an organization’s network is secure. They reveal vulnerabilities in an IT infrastructure and examine the effectiveness of an organization’s security posture. The findings allow an organization to take corrective action before a cybercriminal can exploit any weaknesses.
Depend on Us To:
Identify Vulnerabilities
Validate Security Controls
Guide Remediation Efforts
Provide Third-Party Validation
Cloud Security Services
Secure Your Cloud Assets
As companies increasingly rely on cloud-based services to store and process sensitive data, they need to take proactive and comprehensive steps to safeguard their data.
Cloud Application Security
Actively Defend Your Cloud with MDR Cloud Response
Take your cloud security to the next level by gaining access to 24/7 expert security monitoring and a unified response system. Protect your third-party cloud platform against even the most advanced and fastest types of cyber threats.
Learn MoreCybersecurity Incident Response Services
Effectively Respond to Cyber Events
Incident response services to prepare for, respond to, and recover from cyber incidents. Receive prioritized access to our experienced team and have peace of mind knowing you’ve got a partner ready to handle security incidents and resolve cyberattacks when needed. We’re ready to respond 24×7.
Incident Response Tabletop Exercises
Validate the Effectiveness of Your Incident Response Plans
Test your preparedness in the event of a cyberattack, breach, or other event where technology systems are disrupted. Administrators, technical staff, and others will benefit from participating to strategize how the organization will respond if faced with real security events.
What is a Tabletop Exercise?
A tabletop exercise, also known as a cyber incident response test, is an activity used to evaluate the effectiveness of your organization’s incident response plans. A tabletop exercise aims to examine the client’s internal and external response and coordination efforts following a simulated attack. The exercise intends to improve the client’s understanding of key cybersecurity concepts, identify strengths and weaknesses in response planning, promote changes in attitude and perceptions, and enhance participating stakeholders’ overall response posture and collective decision-making process.
Why do I Need a Tabletop Exercise?
The tabletop exercise helps organizations achieve a deeper understanding of breaches and other threats in a cost-effective way with minimal to no disruption to business operations. It familiarizes top management and other participants with their roles and responsibilities in case of a technology incident. This fosters an understanding of the dependencies and interdependencies among information technology, business continuity, crisis management, and physical security functions.
Virtual Chief Information Security Officer (vCISO) Services
Harness Cybersecurity Expertise Without the Overhead
In search of a CISO? Whether you require part-time support for cybersecurity leadership, are focused on achieving regulatory compliance, or simply need strategic guidance from seasoned security expert, our team is ready to meet your CISO needs.
vCISO Services Solve Challenges Related to:
Cybersecurity Insurance
Difficulty obtaining cyber insurance due to growing requirements of cyber liability insurance providers.
Regulatory Compliance
Struggling to achieve and maintain compliance with increasingly stringent regulations and industry standards.
Sophisticated Cyber Attacks
Navigating the quickly changing landscape and protecting against the rising threat of cyber attacks targeting SMBs and SMEs.
Third Party Risk Management
Managing the security and compliance of third parties, as well as the risks associated with sharing sensitive data and access to systems.
Policy & Plan Development
Comprehensive, Customized IT & Cybersecurity Plans & Policies
Governance work is our thing. After understanding your business requirements, we’ll update or create policies by leveraging our comprehensive policy collection that we’ve crafted and honed over many years.
- Information Security Plans & Policies
- Incident Response Plans & Policies
- Disaster Recovery Plans & Policies
Cybersecurity Services FAQs
Why M.A. Polce for cybersecurity services in NY?
Simply put, we’ve had a security practice for over 20 years and a dedicated staff of certified professionals managing it. Security is at the center of everything we do. We are SOC 2 compliant and follow strict standards for all of our business operations. From assessments to 24x7x365 MDR, we can fully manage or complement your IT operations to maximize your security posture.
What is an MSSP?
A managed security service provider (MSSP) is an outsourced, all-in-one security solution that monitors and manages a business’s security systems. Many organizations partner with an MSSP, often in addition to their existing security program, to protect their network and data from looming cyber attacks.
How do EDR and MDR differ?
Endpoint detection and response (EDR) is the latest industry term that describes what used to be called antivirus. EDR is installed on endpoint devices and attempts to identify known signatures and erratic behaviors that might be indicative of malicious code. Managed detection and response (MDR) is a managed service whereby security analysts in a security operations center (SOC) are actively monitoring, hunting, detecting, and quarantining malicious activity. As such, EDR is more tool-based, whereas MDR is more tool and people based. Both EDR and MDR are essential, and they work nicely together, especially when the telemetry from the EDR agent can be ingested into the MDR process.
How much time does a typical cyber assessment take?
Depending on the scope of the engagement, risk assessments, security assessments, and penetration tests may take 3-6 weeks.
What can I expect from a security assessment?
You can expect a comprehensive analysis of critical systems based on industry best practices. This is done through conversations, a review of system configurations, and the use of advanced tools to hunt for vulnerabilities. Once complete, we will deliver a detailed report outlining our findings, ranked by level of criticality. Recommended action items are identified and clearly explained. Most importantly, we can be engaged for post-assessment remediation if additional assistance is required.
What type of assessment should I start with?
That all depends on the assessment work you’ve already done. Most commonly, the best place to start is with a security assessment. It will reveal all of the vulnerabilities that need to be patched and any configuration settings that should be changed. Once those items are remedied, a penetration test is recommended to see if the bad guys can get in.
Client Feedback
“If you’re in the market for a professional, knowledgeable, and dependable Managed Service Provider, then look no further than M.A. Polce.” – Scott L.
“We have been working with M.A. Polce for the past two years on a tiered approach evaluating our systems, they are very attentive, have a great attention to detail, and have a very professional team. I would encourage any organization to partner with M.A. Polce.” – Jason C.
“We appreciate the partnership that M.A. Polce has brought to our managed IT services. They provide excellent support but also serve as a resource for us to discuss our IT environment and develop plans for improvement, change, and growth.” – Rachel S.
Check Out These Related Cybersecurity Resources
Learn More About How We can Help Protect Your Organization Against Cyber Threats
Reach out for an exploratory conversation about your organization’s cybersecurity and compliance needs.
Set Up a Discovery Session
"*" indicates required fields
Our Technology Partners