Between the growth of cloud services and third-party vendors accessing corporate data to the rise in remote and hybrid work situations, businesses face increasingly complex cybersecurity risks. To accommodate these changes, governments continue implementing regulations for protecting sensitive data. Mounting cybersecurity responsibilities stress the need for well-defined risk management plans. Discover how to craft a solid cyber risk management strategy accounting for various cyber threats.
What Is Cybersecurity Risk Management?
Cybersecurity risk management gives businesses a method for prioritizing and minimizing cybersecurity risks. It helps them identify the threats capable of having the most impact and handle these risks efficiently.
Company-wide cooperation is a key aspect of a cyber risk management plan. Although the IT department implements and oversees cybersecurity measures, every employee must understand and comply with guidelines to reduce risk.
The Components of a Cybersecurity Risk Management Plan
Cyber risk management strategies will vary slightly at each business, as different industries handle different types of information. However, most risk management approaches will feature the following four components:
Identify
You will look at the use of networks and any existing security measures to detect the current threats impacting the business and future risks.
Assess
Once you have identified the risks, you can evaluate the likelihood they will affect operations and the extent of their potential damage.
Control
After estimating how much cybersecurity risk exists or may occur under current practices, you will devise methods and protocols and utilize technologies to lower these risks.
Ongoing Review
Cybersecurity threats change regularly, and a risk management plan should be dynamic. Your cyber risk management strategy requires continuous monitoring to help you modify controls when new threats arise.
What Are Cyber Threats?
A cyber threat is any activity intended to breach security and steal or expose sensitive information. If successful, a cyber threat may cause financial or reputational loss for the company. Common cyber threats include:
Adversarial Threats
These cyber threats are perpetrated by hackers, insiders, third-party vendors, and other malicious actors. Phishing and malware are two of the most frequently used attacks, but there are many more tactics. Businesses often need guidance from cybersecurity experts or trained security staff to navigate these threats.
Human Error
Not every security breach is intentional. Sometimes, honest employees fall prey to phishing schemes or make a mistake when storing files, leading to the exposure of protected data. Although these incidents are innocent, their impact is significant. According to some research, 88% of data breaches stem from human error. Therefore, your business should consider training employees on the various cybersecurity risks to mitigate human error.
System Failure
System failure not only impedes productivity — it can also result in data loss. Retrieving this information is hard without a cyber risk management plan in place. Ensuring your systems run on reliable equipment and regularly backing up data are just two strategies for reducing the impact of system failure.
Natural Disasters
Natural disasters can destroy hardware and digital resources, which may translate into data loss. Using cloud services and distributing storage resources across multiple sites can decrease the threat of natural disasters.
Cyber Risk Management Frameworks
Developing a risk management plan can be challenging, but there are several frameworks businesses can use to begin strategizing. Each format offers standards to help companies identify risk and manage assessment and compliance. Risk management frameworks include:
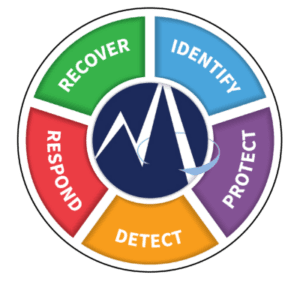
NIST CSF
The National Institute of Standards and Technology (NIST) offers a cybersecurity framework comprised of standards and practices businesses can use to inform cyber risk management. Its guidelines relate to five security functions, including:
- Identify
- Protect
- Detect
- Respond
- Recover
NIST RMF
Also provided by NIST, the Risk Management Framework (RMF) oversees privacy, security, and cyber supply chain risk management for systems and technologies. It features the following steps:
- Prepare
- Categorize
- Select
- Implement
- Assess
- Authorize
- Monitor
ISO 27001
International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) established the ISO/IEC 27001 framework to help organizations manage risk with information systems.
CIS
Center for Internet Security (CIS) also aids businesses in protecting their data from cyber threats with their Critical Security Controls. These 18 measures offer a launching point for organizations to craft effective risk management plans prioritizing threats with the most impact.
Cybersecurity Risk Management for Cyber Insurance
Because of the increasing complexity and frequency of cyber-attacks, your business may still encounter a threat even with a cybersecurity strategy. As such, more organizations are investing in cyber liability insurance to help cover the costs of these attacks.
As with other types of insurance, most providers want to evaluate your level of risk before extending a policy. This practice allows them to establish your premium. For this reason, creating a cyber risk management plan can enhance the value of cyber insurance. The following are two benefits of combining cyber insurance with a risk management strategy:
Increases Chances of Obtaining Cyber Insurance
When you implement clear guidelines to monitor cybersecurity, insurers see your commitment to your risk management responsibilities. As a result, they may be more inclined to provide your business with their services.
Lower Cyber Insurance Costs
Often, insurers will reduce premiums if they believe the organization operates within one of the above frameworks and factors government regulations into their cybersecurity approach.
Learn more about cyber liability insurance coverage, why it’s needed, and what businesses need to do to obtain it. Check out this podcast episode.
Managed Risk and Compliance Services from M.A. Polce
As essential as cyber risk management is, many IT teams are already overwhelmed with tasks, making it difficult to find time to establish and enforce security measures. Additionally, some IT executives lack clear insight into how much security they require.
If your business needs guidance with cybersecurity, turn to M.A. Polce for help. A trusted network security company serving Central and Western New York, we provide comprehensive cybersecurity services to aid organizations with risk management and other functions. For those interested in risk management services specifically, M.A. Polce has a customizable managed risk and compliance service as a part of our assessment and compliance offerings. Some of the deliverables in this service include:
- vCISO consultation
- Risk analysis
- Security roadmap
- External vulnerability scanning
- Policy guidance
- Tabletop incident readiness exercise
For more information on M.A. Polce’s managed risk and compliance service, watch a quick high-level video overview.
Contact us today to learn more about our services and how they can help you navigate cyber risk management.
Sources:
https://hyperproof.io/resource/cybersecurity-risk-management-process/
https://www.comparitech.com/net-admin/cybersecurity-risk-management/
https://csrc.nist.gov/glossary/term/cyber_threat
https://csrc.nist.gov/projects/risk-management/about-rmf
https://www.cisecurity.org/controls/cis-controls-faq
https://www.nist.gov/cyberframework
https://www.auditboard.com/blog/manage-cyber-risk-to-reduce-cyber-liability-insurance-costs/
M.A. Polce partners with Cisco, the global technology giant, to deliver cutting-edge IT and cybersecurity solutions. Their collaboration offers businesses of all sizes access to Cisco’s advanced networking and security technologies, ensuring fortified digital landscapes against emerging threats. M.A. Polce’s certified experts work closely with clients to design bespoke Cisco-based solutions, optimizing efficiency and safeguarding critical data. Together, they provide unparalleled service and support, empowering organizations to thrive securely in today’s interconnected world.