Overview of NYC DOE MOVEit Data Breach
MOVEit is a file-sharing software that private companies and government sectors use to transfer documents and data safely. However, it was recently hacked and leaked data of almost 45,000 students in New York City and millions worldwide.
The released information includes social security numbers, OSIS numbers, dates of birth, and even employee IDs. Some documentation also includes student evaluations and related services progress reports, Medicaid reports for students receiving services, and internal records related to DOE employees’ leave statuses.
The amount of data per person that was leaked varies. But, city officials said they would notify those with compromised data on an unspecified date this summer.
The NYC Department of Education’s Response
On a Sunday following the end of the school year, the New York City Department of Education released a statement about the attack.
“The safety and security of our students and staff, including their personal information and data, is of the utmost importance for the New York City Department of Education. Our top priority is determining exactly which confidential information was exposed and the specific impact for each affected individual,” the department said.
As the release of sensitive information positions victims to be subject to fraudulent activity, the DOE has offered victims access to an identity monitoring service.
After discovering it, the NYC DOE patched the flaw and took their servers offline. Corresponding with those efforts, the NYC DOE is working with NYC Cyber Command to respond to the incident. Additionally, the DOE is cooperating with local and federal law enforcement agencies to investigate the incident.
Who is responsible for the MOVEit ransomware attack on the DOE?
Sources suspect the attack was conducted by CL0P, a ransomware gang with pro-Russian ties. In fact, the gang has claimed responsibility for the MOVEit data-theft attacks in a statement shared directly with BleepingComputer in early June 2023.
A noteworthy story component is that CL0P threat actors did not immediately use the data to extort any NYC DOE victims after obtaining the data. At this point, the CL0P has not published any DOE information. The group also has not threatened to or demanded payment. Likely, the group is still sifting through the files to determine what is most valuable to them.
Other MOVEit Data Breaches
The NYC DOE breach is merely an addition to the already extensive list of breaches the gang has carried out. Compared to the other organizations affected by the same file transfer software breach, the scale of NYC DOE is relatively small. But, what’s most notable about this case is the involvement of the personal information of minors.
CL0P revealed they had breached the servers of “hundreds of companies,” including the largest US pension fund, Calpers, and insurer Genworth Financial. Hackers were led to both organizations via a path provided by a third-party vendor, PBI Research Services. Concerning those attacks and others, by late June, the number of MOVEit hack victims grew by several million.
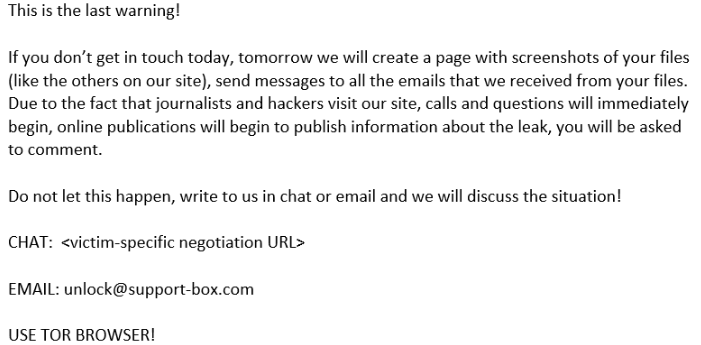
In previous CL0P attacks, the group emailed their extortion demands to company executives.
But, with those affected by the MOVEit Transfer attacks, CL0P is taking a different approach. Instead of demanding ransom, CL0P wants affected organizations to contact them if they desire to negotiate a ransom.
The CL0P Ransomware Group
According to a joint Cybersecurity Advisory from CISA, open source information indicates CL0P (also known as TA505) began exploiting the previously unknown SQL injection vulnerability (CVE-2023-34362) vulnerability on May 27, 2023. This took place in Progress Software’s managed file transfer (MFT) solution known as MOVEit transfer. Once exploited, the group infected MOVEit Transfer’s internet-facing web applications with a web shell named LEMURLOOT. This was then leveraged to steal data from underlying MOVEit Transfer databases.
The CL0P ransomware group has shown a common tactic of working on holidays. This is significant because holidays are typically associated with fewer staff members on the clock. Meaning holidays are an opportune time to attack without getting caught.
How to Defend Against Ransomware
If you become a victim of ransomware and/or extortion, experts strongly advise you never to pay for your data back. If your data is stored in an encrypted location, it will make it more difficult for the threat actor to view and use it against you. Additionally, paying will encourage the attackers, and others like them, to do it again.
In summary, organizations need to protect their most crucial assets. While there is no fool-proof way to eliminate all cyber risks, you can mitigate most with basic security initiatives. Options include maintaining a patch schedule and regularly completing vulnerability assessments.
If your organization could use assistance implementing cybersecurity or managing cyber risk, consider partnering with a cybersecurity company like M.A. Polce. As a managed security services provider (MSSP) with industry-leading Managed Detection and Response capabilities, we can help protect your organization from cyber threats like ransomware. You can contact us today to discuss your needs.