Overview of Akira Ransomware
A new ransomware operation named Akira has generated a list of victims in different industries, such as education, finance, real estate, manufacturing, and consulting. In two months since its launch, Akira claims attacks on at least sixteen companies and counting, according to BleepingComputer. The operation’s primary focus is to breach corporate networks worldwide, encrypt the files, and demand millions of dollars in ransom.
Due to code differences, experts believe that this new Akira operation is unrelated to a former ransomware strain with the same name active in 2017.
How Akira Ransomware Works
Akira has a simple technique that can easily take down a company or organization by encrypting its files. Akira Ransomware runs a PowerShell command and deletes Windows Shadow Volume Copies on the device. Once the command is successfully run, the ransomware starts to encrypt files on the device of over 150 different file extensions. During the encryption process, it passes over any files found in the Recycle Bin, System Volume Information Boot, ProgramData, and Windows folders. It also skips encryption on files ending in .exe, .lnk, .dll, .msi, and .sys. When successfully encrypted, the files show with the extension.akira at the end of the file name, similar to “example.doc.akira” or “example.jpg.akira.”
Akira also takes advantage of the Windows Restart Manager API to shut down Windows services or close out processes that keep a file open, forcing the file to be overpowered and encrypted. Each computer folder contains a ransom note left by Akira, named “akira_readme.txt”, which includes information on how the files were taken over and encrypted, along with links to the Akira data leak site and a site where negotiations take place to pay the ransom. Each victim has a unique negotiation password that can be entered into Akira’s Tor site on the dark web. This leads the victim to a chat system where they can negotiate with the ransomware group.
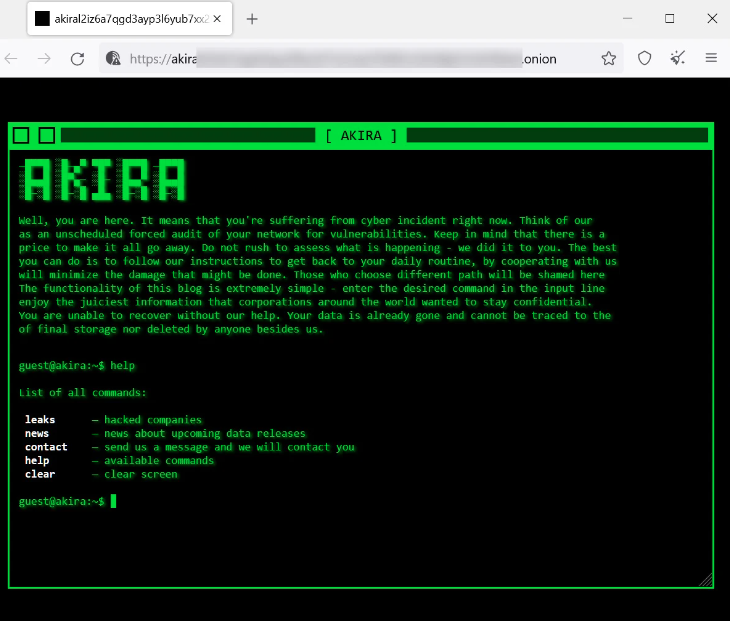
Akira Ransom Note on Data Leak Site. Source: BleepingComputer
How and Why Akira Steals Corporate Data
Once it successfully breaches a network, Akira takes advantage of the compromised organization. It does this by spreading laterally to other devices within the organization. Once Akira gains the Windows domain admin credentials to the organization, the group deploys ransomware throughout the network. But not before they steal corporate data for leverage. Akira uses the stolen data to extort the company. In other words, the group teases the victim with threats to release the information publicly if a ransom is not negotiated and paid.
Akira has successfully leaked the data of four victims on its personal data leak site. The leaks contain data ranging from 5.9 GB to 259 GB. Meanwhile, ransom demands range from $200,000 to a few million dollars. However, in some cases, companies don’t need their files decrypted. Instead, they solely want to protect the confidentiality of their information. In instances where decryption isn’t needed, ransom demands have been lowered but not completely removed. Any weaknesses are being monitored for Akira Ransomware at the moment as it is relatively new.
How to Protect Your Organization from Akira Ransomware
You can help protect your organization from Akira Ransomware similarly to how you would from other cyber threats. A few basic best cybersecurity practices include:
- Practicing good IT hygiene
- Backup your data on a regular basis
- Invest in Security Awareness Training for yourself and your employees
- Ensure applications, software, and appliances are up to date/patched
As a Managed Security Service Provider (MSSP) in New York State, M.A. Polce specializes in providing comprehensive, customizable cybersecurity services to protect businesses from cyber threats like Akira Ransomware. If your organization needs assistance managing IT security, contact us today.
Sources
https://www.bleepingcomputer.com/news/security/meet-akira-a-new-ransomware-operation-targeting-the-enterprise/ – See the Example Ransom note here.
https://thecyberexpress.com/mcgregor-cyber-attack-akira-ransomware-group/
https://news.sophos.com/en-us/2023/05/09/akira-ransomware-is-bringin-88-back/


