In today’s business world, cybersecurity has become a top priority for virtually all industries. Federal Bureau of Investigation Internet Crime Report claims over 800,000 cybercrime complaints totaling $10.3 billion in 2022.
These circumstances have led to the rapid growth of the managed detection and response (MDR) services market. MDR services enable businesses to outsource cybersecurity functions to a security operations center (SOC). Using MDR services, an organization can augment its approach to cyber threat detection and incident response.
With cyber-attacks becoming more complex and the MDR marketplace developing, businesses may encounter misconceptions about these services. Distinguishing between fact and fiction is vital for choosing the best IT solutions for your business. Learn the truth about MDR services from M.A. Polce.
Understanding MDR
MDR services make advanced cybersecurity solutions accessible to organizations that cannot afford to hire additional IT staff, such as small to medium-sized businesses (SMBs). These service providers have expertise in actively hunting for, detecting, containing, analyzing, and ultimately reducing cyber threats. They also utilize a range of tools to understand cybercriminal tactics’, such as encryption and authentication/authorization solutions and antivirus programs.
MDR service providers also have extensive knowledge of threat detection, enabling them to uncover the main cause of intrusions to prevent them. Businesses rely on the guidance of their MDR providers to augment organizational security and potentially boost profitability.
Managed detection and response is one of several cybersecurity solutions, but companies will find it offers unique features. Some of the key components of MDR include:
- Service providers utilize their own technologies and tools, so businesses don’t need to spend more money on resources.
- The focus is more on threat detection than verifying a business meets compliance regulations.
- Service providers are capable of remote response and incident validation.
- MDR services incorporate a human element for monitoring, analysis, and continuous communication.
Misconceptions About Managed Detection and Response
There are many myths about MDR services, including how they work, their cost, and what types of businesses can use them. Consider these common misconceptions and the realities to make a more informed decision:
It’s Expensive to Adopt
Businesses may avoid MDR services out of fear about their cost. However, most MDR services are SaaS solutions and require no capital investment or additional hardware. What’s more, MDR providers can often combine the tools and services necessary for cybersecurity, helping save time and money.
Finally, when MDR services help organizations achieve a stronger cybersecurity posture, they’re better equipped to detect and respond to threats, reducing downtime following incidents and the chance for future occurrences.
Not Designed for Small Businesses
SMBs may think their size means cybercriminals aren’t interested in attacking them. In truth, SMBs are just as susceptible to cyber threats as large corporations, if not more so, because they often lack the resources to maintain higher cyber maturity.
Deloitte’s 2023 Global Future of Cyber Survey found that organizations with low cyber maturity are more likely to experience more significant threats than those with high cyber maturity overall. MDR services benefit businesses of all capacities but can be particularly helpful for small enterprises.
Every MSSP Offers MDR Services
Not all managed security service providers deliver MDR solutions. Additionally, there’s no standard solution that works for every business. Before searching for a provider, assess your current capabilities, future goals, and your customers’ concerns to establish your MDR needs. Then pinpoint a trustworthy provider that can deliver these tailored services.
What are the benefits of MDR?
Some estimates claim that 50% of businesses will use MDR services by 2025. The growing demand for these services can be explained by the many advantages they offer organizations, such as:
- Reducing the traditional challenges of developing and maintaining an advanced security infrastructure
- Eliminating the need for businesses to hire additional IT staff
- Accessing intelligence from security professionals well versed in the latest cybersecurity threats
- Giving IT departments more time to devote to strategic initiatives
Partnering with an MDR service provider can also enable a business to save money. Because providers use their own resources, it keeps your company from needing to invest in MDR tools and technologies to achieve more robust cybersecurity.
MDR services produce distinct advantages for different industries and individual businesses. When researching a service provider, be sure to check out the success stories or testimonials on their website for a better idea of the types of organizations they serve.
How to Choose the Right MDR Provider
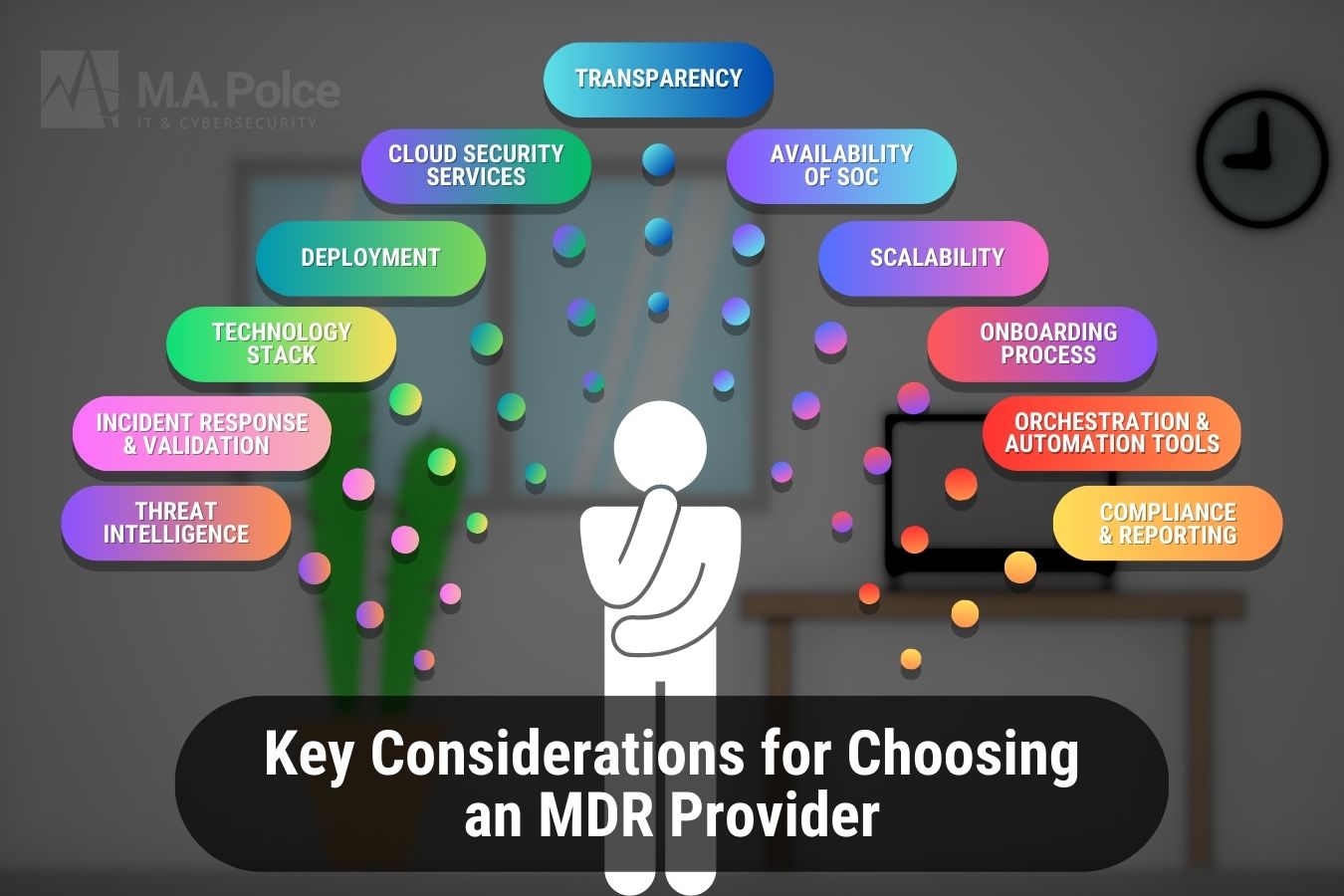
As mentioned, there’s no one-size-fits-all MDR solution for every organization. Your business must evaluate the different options to determine how effective each provider might be at helping you achieve your goals. The following are key elements to consider when making your assessment:
- Threat intelligence
- Incident response and validation
- Their technology stack
- Onboarding process
- Cloud security services
- Orchestration and automation tools
- Transparency
- Availability of SOC/communication
- Deployment
- Compliance and reporting
- Scalability
What to Look for in an MDR Solution
In a market flooded with MDR solutions, it can be challenging to decide on what MDR will work best for your environment. Chief Architect Nick Polce understands these challenges as M.A. Polce went through the selection process a few years ago. To settle on an MDR solution that would best fit the needs of M.A. Polce’s clients, Polce said an extensive vetting process was necessary. Reflecting on this experience, Polce weighed in with three qualities that make MDR solutions stand out from the crowd:
-
“They are able to detect tradecraft techniques that EDRs can’t detect. We discovered a lot of “MDR” providers simply took an EDR platform, slapped “managed” before it, and went to market. This won’t help address the issue of tradecraft. This is why that roughly 70% of alerts our MDR triggers on never have a corresponding EDR alert!
-
They are able to deliver the service without compromising the security of a mobile workforce and cloud users. Many of the MDR solutions out there are dependent on a physical or virtual appliance for inspection purposes. This poses a single point of failure and can become quite costly. We needed something that could protect users wherever they are and not be required to route traffic through a centralized sensor. Additionally, over 50% of the alerts our MDR triggers on are within the M365 space so ensuring we could protect these users and workloads was also critical.
-
They are simple and efficient to deploy. As rudimentary as this sounds, we found this to be extremely important. Complex deployments that require multiple parties, client specific configurations, hardware dependencies, and multiple different licensing structures invite the opportunity for misconfigurations, failures, and other items that leave our customers vulnerable. Our MDR solution can be deployed within minutes to begin protecting clients.”
Questions to Ask Potential MDR Providers
Once you settle on several MDR service providers and get the chance to meet with them, having questions ready can help you figure out the best option. Some questions to ask include:
- What is your threat detection model, and how does it help mitigate risk?
- What does deployment look like? Will it require the business to replace existing tools?
- How do you handle data from a security event?
- How much of the attack surface can you protect?
- What is your approach to safeguarding different IT resources?
- How do your services integrate into business operations?
- What does your response strategy look like following a significant event?
- Will you adapt your service as the business experiences new cyber risks?
- How do you recruit and train your security professionals?
- How much do your MDR services cost? What is your pricing model, and how does it balance with scalability?
Find a Reliable MDR Service Provider
As cyber threats grow, the need for reliable cybersecurity services like managed detection and response will only increase with them. When you attain MDR services, you have a more proactive means for detecting, containing, analyzing, and mitigating cyberattacks. The results are a more effective cybersecurity infrastructure that protects sensitive information and enables you to save time and money on many IT tasks.
For MDR services from a provider dedicated to meeting its client’s needs, choose M.A. Polce. We’re a SOC 2-compliant managed services provider (MSP) and managed security services provider (MSSP) that delivers high-quality, cost-effective IT and cybersecurity solutions for SMBs across New York State. Contact us today to learn more about our cybersecurity services like MDR for small and medium-sized businesses.
Sources
https://www.gartner.com/reviews/market/managed-detection-and-response-services
https://www.msspalert.com/cybersecurity-guests/demystifying-mdr-five-myths-for-mssps/
https://www.business.att.com/content/dam/attbusiness/guides/mdr-evaluators-guide.pdf
https://www.fortinet.com/resources/cyberglossary/managed-detection-and-response
https://venturebeat.com/security/xdr-vs-mdr-how-to-pick-the-right-one-for-your-security-needs/