In today’s digital landscape, where cyberattacks grow more sophisticated and persistent, businesses face an ever-present threat. Reacting after an attack is no longer sufficient; proactive measures like regular vulnerability assessments and penetration tests are essential. These practices, when integrated into a comprehensive vulnerability management program, help organizations stay ahead of cybercriminals and safeguard their most critical assets.
Understanding the Role of a Vulnerability Management Program
A well-structured vulnerability management program is crucial in proactively defending an organization against the rising tide of cyber threats. By continuously identifying and mitigating vulnerabilities, this program reduces the attack surface, making it more difficult for cybercriminals to exploit weaknesses. Addressing these vulnerabilities before they can be leveraged by attackers significantly lowers the risk of successful cyber incidents.
From a regulatory perspective, a vulnerability management program is vital for ensuring compliance with key regulations like HIPAA, GDPR, and PCI DSS. Regularly addressing security gaps not only maintains compliance but also simplifies audit processes by providing comprehensive documentation that demonstrates readiness. This preparation makes passing audits more straightforward and helps avoid costly penalties.
Furthermore, when it comes to cyber insurance, a robust vulnerability management program can be a game-changer. Insurers view such programs as evidence that an organization is actively managing its cybersecurity risks. This proactive approach can lead to better insurance terms, including lower premiums or higher coverage limits. Additionally, meeting the security standards required by insurers is crucial for securing coverage and avoiding potential claim denials in the event of a cyber incident.
The Synergy Between Vulnerability Scanning and Penetration Testing
Regular vulnerability scans and penetration tests are integral to an effective vulnerability management program. These two practices work together to identify, assess, and mitigate security risks within an organization’s IT infrastructure.
Vulnerability scanning is an automated, continuous process that scans an organization’s systems, networks, and applications to detect known vulnerabilities, such as outdated software, misconfigurations, and missing patches. These scans provide a broad overview of the organization’s security posture, enabling IT teams to address issues before they can be exploited. Typically performed on a frequent basis, vulnerability scanning ensures that newly discovered vulnerabilities are promptly identified and managed.
In contrast, penetration testing (pen testing) is a more targeted and manual approach. Ethical hackers simulate real-world cyberattacks to exploit both known and unknown vulnerabilities. Pen testing delves deeper into the security environment, uncovering complex vulnerabilities that automated scanners might miss, such as logic flaws or zero-day vulnerabilities. This method also evaluates how effectively existing security controls can withstand an actual attack, providing a more comprehensive understanding of potential risks.
By combining these methodologies, organizations can adopt a layered approach to security. While vulnerability scanning offers regular, automated insights into potential weaknesses, pen testing provides in-depth analysis and validation of defenses. This combination ensures that vulnerabilities are not only identified but also thoroughly understood and effectively mitigated, allowing organizations to continuously improve their security posture and stay ahead of evolving threats.
Compliance Requirements for Vulnerability Scans and Penetration Tests
Certain industries, such as healthcare, finance, education, and government, are particularly attractive targets for cyberattacks due to the sensitive nature of the data they handle. As a result, these sectors are governed by strict regulations that mandate regular assessments and testing to protect data integrity and privacy. These requirements are often driven by regulatory bodies or industry standards, such as the NIST Cybersecurity Framework (CSF), which recognizes the critical importance of proactive cybersecurity measures. Non-compliance can lead to severe legal penalties, financial losses, and irreparable damage to an organization’s reputation.
Industry-Specific Requirements
- Healthcare: Under regulations like HIPAA, specifically the HIPAA Security Rule, healthcare organizations must regularly assess their security risks to protect patient data.
- Finance: The financial sector, regulated by frameworks like PCI DSS and the Gramm-Leach-Bliley Act (GLBA), requires stringent security measures, including regular testing, to safeguard financial information.
- Retail: Retailers processing credit card payments must comply with PCI DSS, which mandates regular vulnerability assessments and penetration testing.
- Government: Public sector organizations are often required to adhere to standards like NIST, which includes requirements for regular security assessments.
- Education: Institutions handling sensitive student information are increasingly required to demonstrate strong cybersecurity practices, often including regular assessments.
The Benefits of Regular Vulnerability Scans and Penetration Tests
Even for businesses not legally obligated to perform regular scans and tests, there are numerous benefits to adopting these practices as part of a proactive cybersecurity strategy.
- Identify Unknown Weaknesses: Vulnerability scans can uncover weaknesses that might otherwise go unnoticed until exploited by attackers. Penetration tests take this a step further by simulating real-world attack scenarios, providing insights into how a system would hold up against an actual attack.
- Strengthen Security Posture: By continuously assessing and testing security controls, organizations can address vulnerabilities as they arise rather than waiting for a breach to occur.
- Boost Customer and Partner Confidence: Demonstrating a commitment to cybersecurity through regular assessments can enhance trust and credibility with clients, partners, and stakeholders.
- Optimize Security Investments: By identifying and prioritizing vulnerabilities, businesses can make more informed decisions about where to allocate resources for maximum impact.
The Critical Need for Strategic Cybersecurity Guidance for Vulnerability Management
Identifying vulnerabilities is only the first step in a comprehensive cybersecurity strategy. To truly protect an organization, strategic cybersecurity guidance is essential for navigating the remediation process. Without expert advice, businesses may struggle to prioritize efforts and allocate resources effectively. In turn, they could be left vulnerable to attacks despite their best intentions. Strategic guidance is crucial for translating assessment findings into actionable steps that enhance security resilience.
Overcoming Resource Challenges for Small and Mid-Sized Businesses
For many small and mid-sized businesses, limited resources make it challenging to maintain an effective cybersecurity program. Without the in-house expertise or budget to conduct regular assessments and address the findings, these organizations are at significant risk. This is where a Virtual Chief Information Security Officer (vCISO) service can be a game-changer—a cost-effective solution that provides the strategic guidance and expertise needed to protect against evolving threats and ensure compliance with regulatory demands.
» Don’t have a Chief Information Security Officer? Download our eBook, Five Tips to Keep Your Organization Protected & Compliant without an In-House CISO
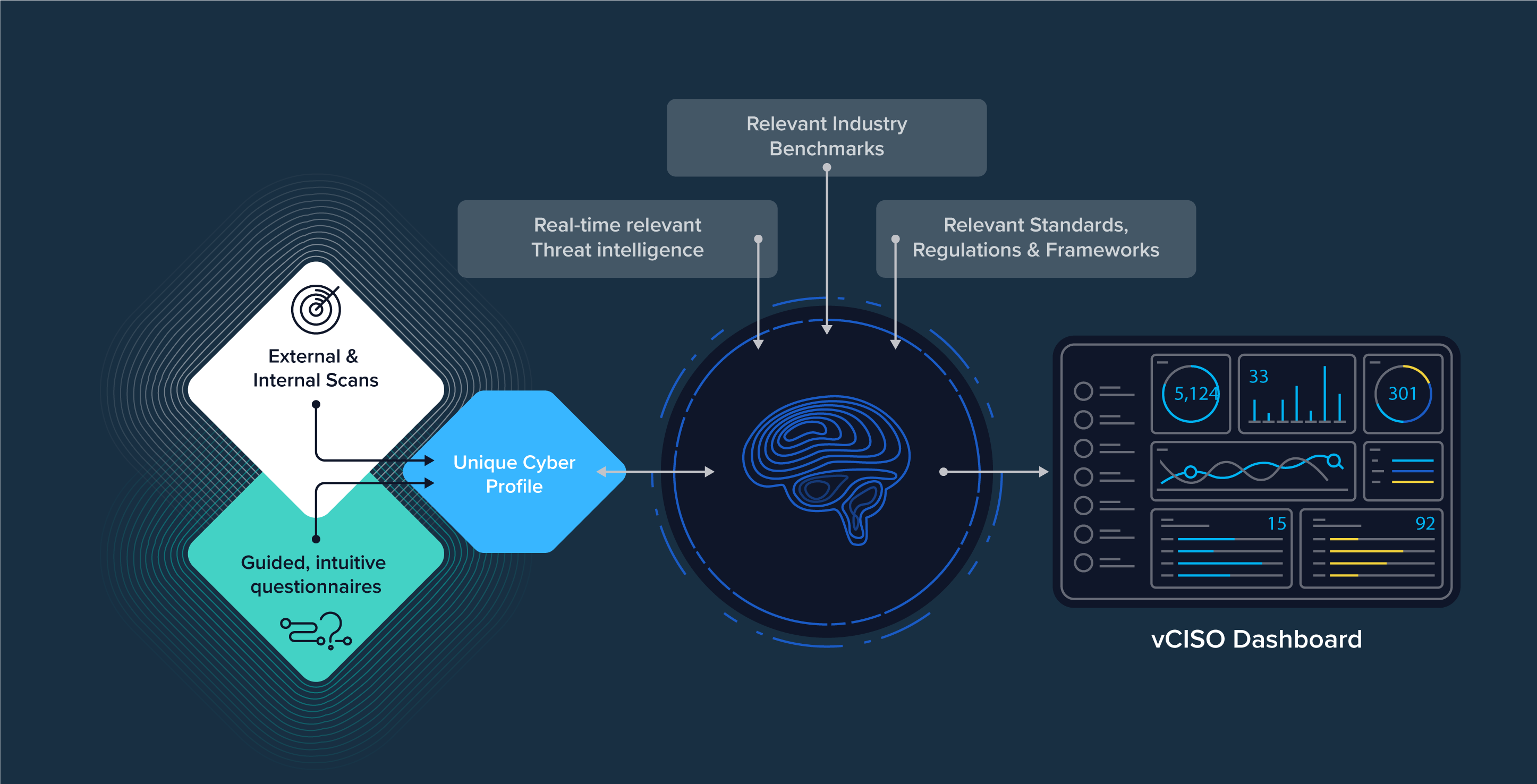
Unlocking the Power of vCISO Services for Vulnerability Management
A vCISO is a professional who provides the guidance, skillset, and knowledge needed to fill the gaps in a resource-deficient cybersecurity program. Acting as a part-time or on-demand member of your team, a vCISO offers strategic advice and oversees the implementation of cybersecurity measures without the overhead of a full-time cybersecurity executive.
Key Benefits of vCISO Services:
- Realize Current Security Posture: Gain a clear understanding of your current security posture, including strengths, weaknesses, and areas for improvement.
- Mitigate Security Risks: Work with experts to identify and mitigate security risks before attackers can exploit them.
- Receive a Custom Security Roadmap: Develop a tailored security roadmap based on your current and desired level of cyber maturity, ensuring that your security efforts are aligned with your business goals.
- Improve Compliance: Ensure that your organization meets all relevant regulatory requirements, avoids legal penalties, and demonstrates a commitment to security.
- Maintain Security Resilience Over Time: Regular assessments and ongoing strategic guidance help ensure that your security measures remain effective in the face of evolving threats.
- Lay the Foundations of a Robust Cyber Program: Build a strong cybersecurity foundation that can be expanded and strengthened over time, adapting to new challenges as they arise.
- Harness Cyber Expertise at a Fraction of the Cost: A vCISO service allows you to harness expert cybersecurity knowledge and experience without the cost of a full-time executive, making it an ideal solution for small and mid-sized businesses.
Proactively Manage Security Vulnerabilities with M.A. Polce’s vCISO Services
In today’s cyber landscape, vulnerability scans and penetration tests are not just regulatory obligations or best practices. Now, they are essential mechanisms for maintaining a robust security posture. However, identifying vulnerabilities is only half the battle. With strategic guidance from a vCISO, businesses can effectively address these vulnerabilities, ensuring long-term resilience and compliance.
M.A. Polce offers vCISO services as part of a broader governance, risk, and compliance (GRC) solution. Our program equips businesses to elevate their cyber risk management strategies, systematically tackling cyber threats. Through a series of assessments and scans, we create a complete profile of your current risk level and cyber posture compared to industry benchmarks. From there, we provide expert guidance to remediate weaknesses and help you achieve your desired level of compliance. If you want to manage cyber risk with a custom-built program, contact us to learn more.