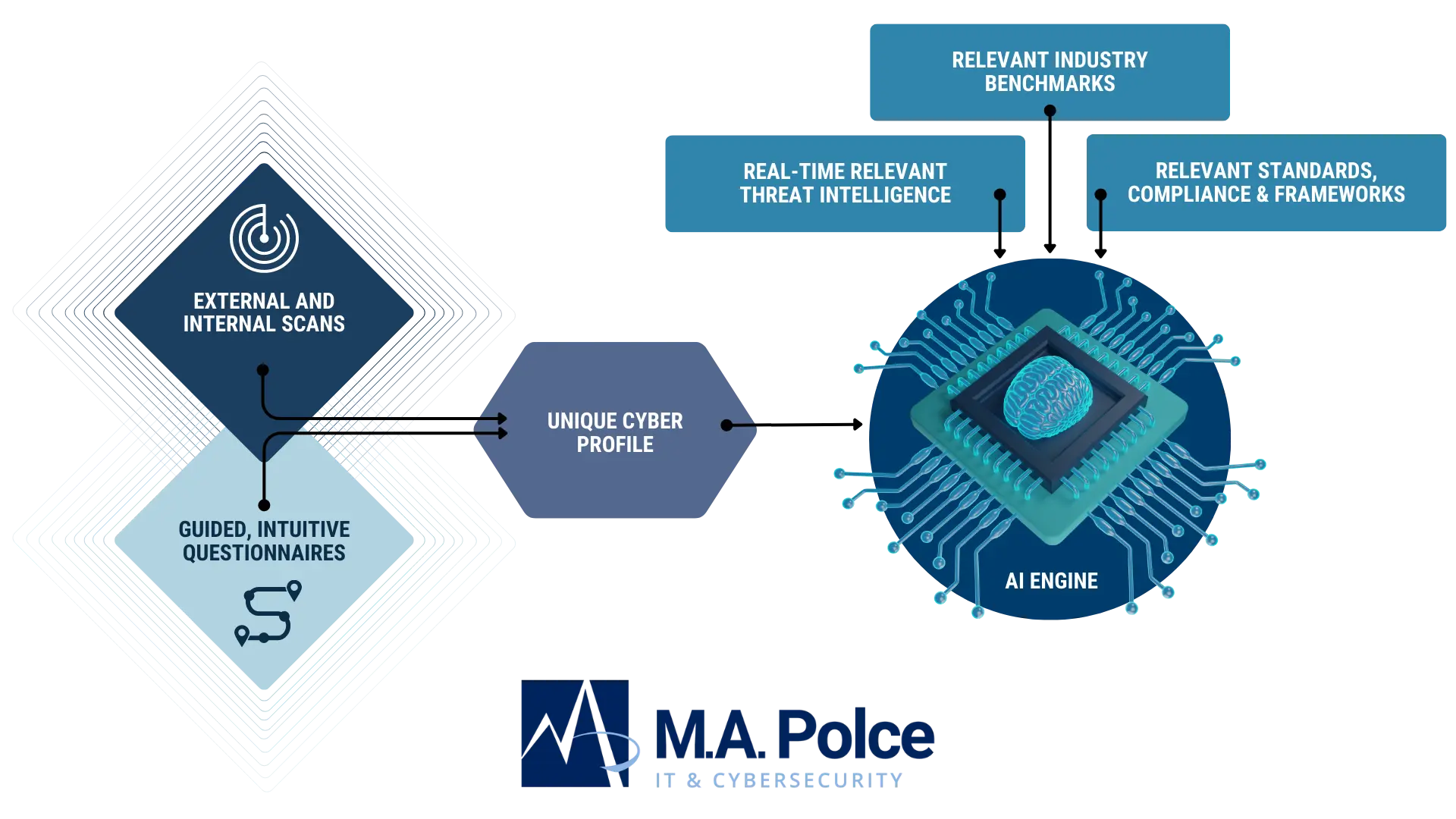
Streamline Compliance and Enhance Your Security Posture
Move beyond ad-hoc risk mitigation efforts. Our program identifies and addresses sources of risk systematically, ensuring a proactive approach to cyber risk management aligned with your governance, risk, and compliance initiatives.